Did you know ?
Public SSL/TLS certificates provisioned through AWS Certificate Manager are free. You pay only for the AWS resources you create to run your application.
AWS issued public certificates can be used with service such as
- CloudFront
- Elastic Load Balancing
- API Gateway
- Amazon Cognito
- AWS Elastic Beanstalk
- AWS App Runner
- AWS Nitro Enclaves
- AWS CloudFormation
- AWS Amplify
- Amazon OpenSearch Service
To create a certificate go to
AWS Certificate Manager > Certificates > Request Certificate > Request public certificate
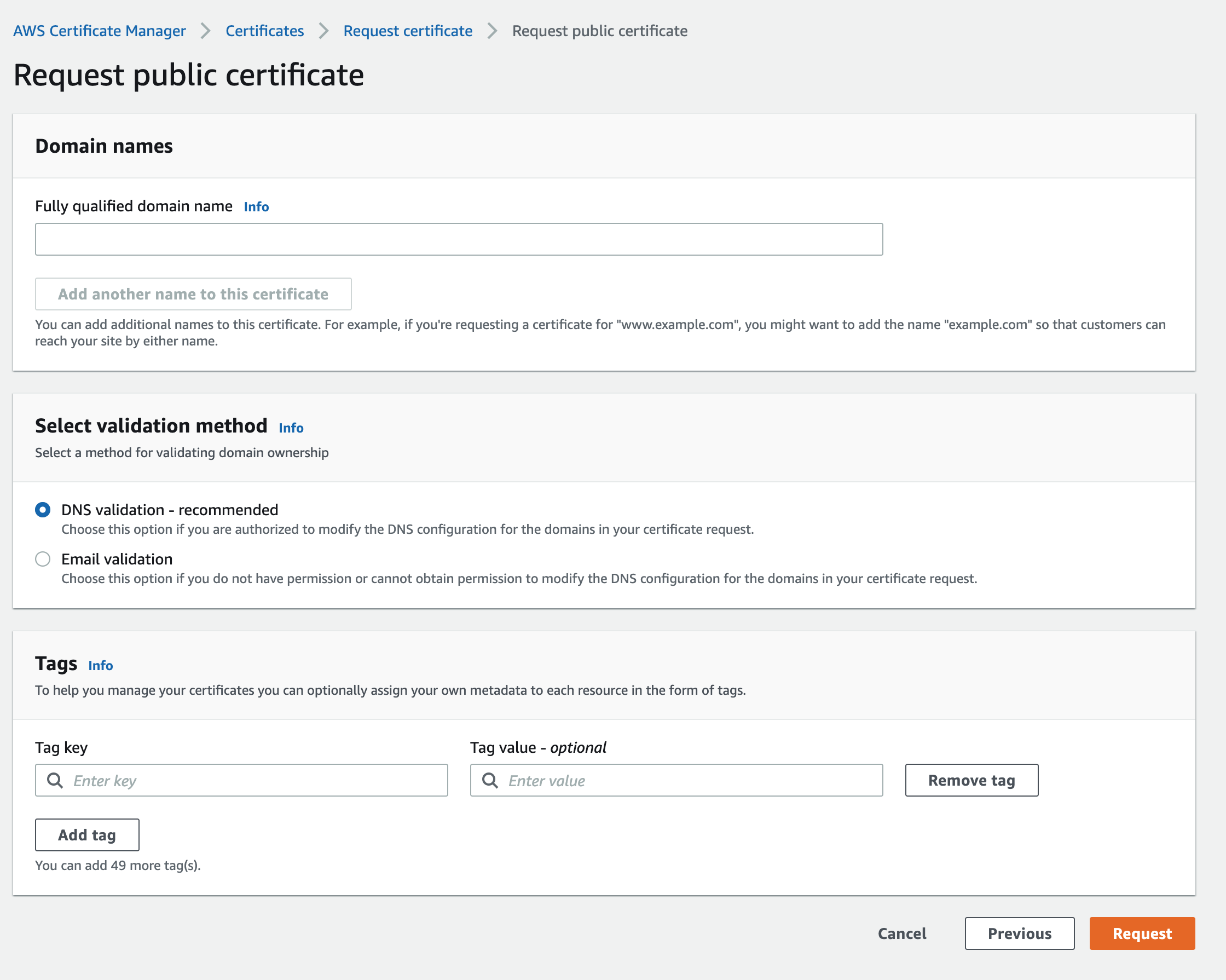
AWS validates the ownership of domain by two methods
- DNS Validation
- Email Validation
Before the Amazon certificate authority (CA) can issue a certificate for your site, AWS Certificate Manager (ACM) must prove that you own or control all of the domain names that you specify in your request. Ownership of domain can be proven by either Domain Name System (DNS) validation or with email validation at the time you request a certificate.
Steps to validate ownership by DNS validation
- Open the ACM console at https://console.aws.amazon.com/acm/.
- In this page, choose the Certificate ID of a certificate with status Pending validation that you want to configure. You will be taken to details page.
- In the Domains section, complete one of the following two procedures:
- (Optional) Validate with Route 53.An active Create records in Route 53 button appears if the following conditions are true:
- You use Route 53 as your DNS provider and you have permission
- Your FQDN has not already been validated.NoteIf you are in fact using Route 53 but the Create record in Route 53 button is missing or disabled, Choose the Create records in Route 53 button, then choose Create records. The Certificate status page should open with a status banner reporting Successfully created DNS records.Your new certificate might continue to display a status of Pending validation for up to 30 minutes.TipYou cannot programmatically request that ACM automatically create your record in Route 53. You can, however, make an AWS CLI or API call to Route 53 to create the record in the Route 53 DNS database.
- (Optional) Follow this if you are using Route 53 as your DNS provider and using 3rd part DNS provider like godaddy ,
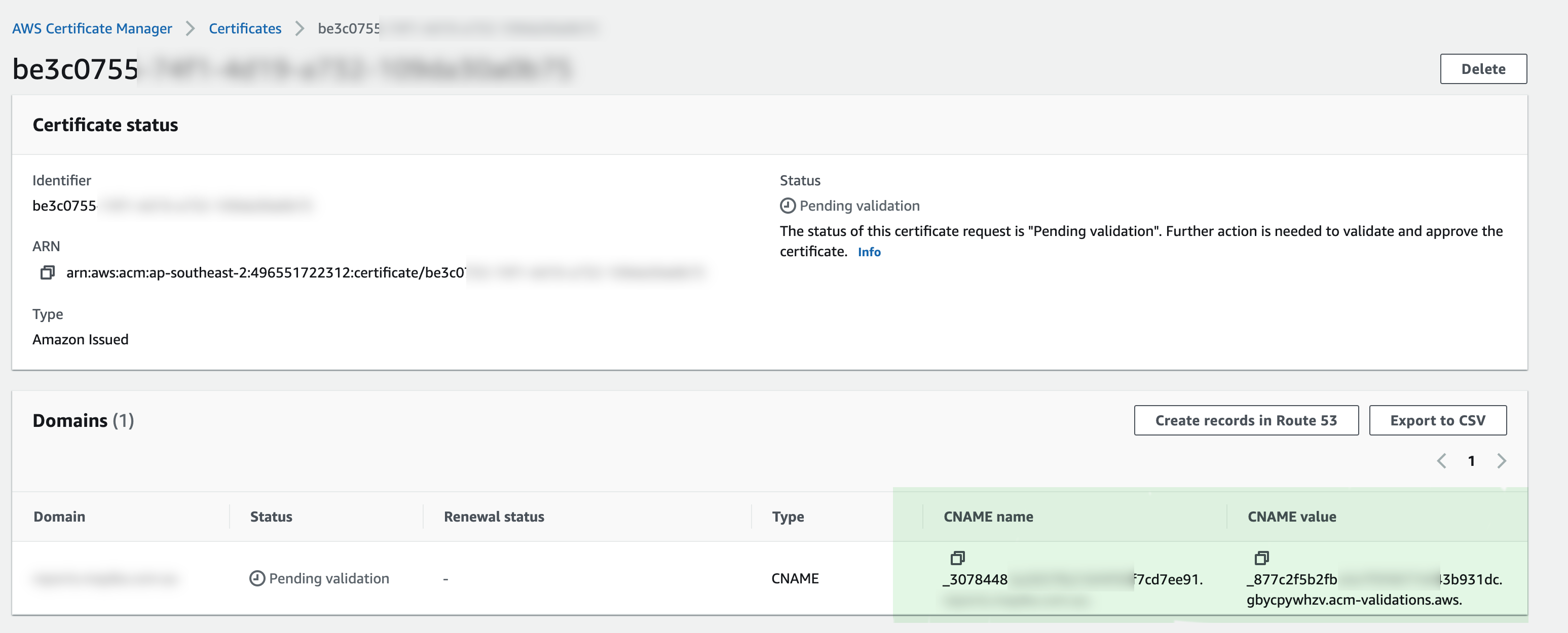
- get the CNAME information and add it your DNS database. On the details page for the new certificate, you can do this in either of two ways:
- Copy the CNAME components displayed in the Domains section. This information needs to be added manually to your DNS database.
- Alternatively, you can choose Export to CSV the DNS configuration. In this file you will have domain name, Record Name and Record Value to be added to DNS zone file to validate the domain
- get the CNAME information and add it your DNS database. On the details page for the new certificate, you can do this in either of two ways:
- (Optional) Validate with Route 53.An active Create records in Route 53 button appears if the following conditions are true:
As you can see in the following image, where to find CNAME record name and CNAME record value to update DNZ zone file to validate certificate
If you don’t have access to edit DNS Zone file, consider email validation yet DNS validation is recommended
When you are adding CNAM for some DNS provider you do not need to enter complete domain for CNAM such as abc.example.com instead you just need to enter abc, check this configuration with DNS provider.
After adding CNAME check if it is working by using dig or nslookup command
To lookup CNAME try the following dig command
dig abcx.google.com CNAME Some times it takes time to update or propagate DNS update based on DNS TTL value
To use custom domain with API gateway you need to create the custom domain first and without public certificate it is not possible to create custom domain for API gateway. Assuming you have created custom domain, you will see the endpoint configuration to configure CNAME in the section of custom domain names endpoint configuration



Leave a Reply